FAQ: General Questions & Answers
What is GoodCrypto?
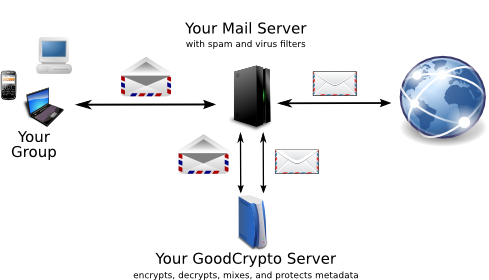
One server that protects the privacy of everyone in your organization
GoodCrypto is a private server that runs on your computer which protects email and browsing for a group. It automatically encrypts and decrypts email including metadata, and manages keys. Everyone in the group gets Tor anonymity plus malware blocking and tracker removal. GoodCrypto is based on the most tested and trusted crypto, GPG and Tor. Snowden relied on them, and he is alive and free. It's hard to imagine a better test.
Why do I need GoodCrypto?
It's easy to think that when you exchange an email message or browse the web in the privacy of your office or home, no one else can see it. Prior to Edward Snowden's revelations, most of us probably thought economic espionage was just a Hollywood story line, not reality. Just a small sampling of recent news stories shows us how wrong that misconception was.
- Edward Snowden tells German TV that NSA is involved in industrial espionage. (Censored. Copies 1, 2, 3, 4)
- US and Canadian spies have targeted Brazilian companies, Petrobras and Energy and Mining Ministry.
- The Australian spy agency helped BHP negotiate trade deals.
- The Guardian reported that XKeyscore is an NSA tool that collects "nearly everything a user does on the internet".
GoodCrypto stops spies from reading your email in transit and watching where you surf on the web.
What are the benefits?
Protect privacy
- Happier users. Same browser. Same mail.
- Properly configured. Strong crypto.
- Resist censorship.
- No clicks and no training for users.
- Safety in numbers. Hide in a crowd, and hide your crowd in a bigger crowd.
- Right software. Right versions.
- Pre-configured.
- Automatic updates. Professional support.
- Secure infrastructure. Integrated solution.
- Hardened. Performance-optimized.
- Layered protection.
- Easy to install, use, and maintain.
- Virtual appliance. (soon)
Why should I pay for open source?
- You get the fastest security updates possible.
- You get the newest features first, typically 6 months or more before non-subscribers
- You're not vulnerable while you wait for the next source release.
- You don't have to build and integrate updates manually.
- You help finance continued development.
- You get professional support. No finger pointing. Just solutions.
How do I know if the threat is real?
"America’s long-standing ability to disrupt the financial networks of its foes and even permanently upend parts of the global financial system". The U.S. goal is to "starve them."
- U.S. National Intelligence Director James Clapper admits that the U.S. spies on "financial matters" .
- Ed Snowden revealed that "These programs were never about terrorism: they’re about economic spying, social control, and diplomatic manipulation. They’re about power."
- Edward Snowden tells German TV that NSA is involved in industrial espionage. Censored. Copies 1, 2, 3, 4, 5
- The NSA Is Building the Country's Biggest Spy Center. Priorities are "financial information, stock transactions, business deals"
- GCHQ captured emails of journalists from top international media. 70,000 emails harvested in less than 10 minutes.
- N.S.A. Collecting Millions of Faces From Web Images and from email for facial recognition.
- Inside the NSA’s secret Utah data center "capable of sorting through and storing every e-mail"
- NSA's Utah Home "designed to store massive amounts of information gathered secretly from phone calls and emails"
- XKeyscore: NSA tool collects 'nearly everything a user does on the internet'
- Russia and China are hacking British companies and spying on their employees. A “major London listed company”, said to be Rio Tinto, lost a staggering £800m as a result of a “hostile state cyber attack”
- Cyberspace Becomes Second Front in Russia’s Clash With NATO. Targets include the Polish stock market, a German steel plant, etc.
- How Covert Agents Infiltrate the Internet to Manipulate, Deceive, and Destroy Reputations. Snowden documents include how to "Discredit a company"
- Inside the Red Web: Russia's back door onto the internet. Able to "silently and effortlessly eavesdrop on emails".
- "Chinese economic espionage is so severe that stopping that is more important than being able to read the communications of a criminal,” said Mike McConnell, former NSA Director.
- China Is Still Hacking US Companies After Promising It Would Stop, Report Says
- Inside the Chinese Boom in Corporate Espionage
- China’s Growing Spy Threat One estimate is "there are around two million Chinese working directly or indirectly for China’s intelligence apparatus."
- Russia, China engaging in industrial espionage
- NSA asked Germany ‘to spy’ on Siemens
- "The Americans weren't just interested in terrorism; they also used their technical abilities to spy on companies and agencies in Western Europe."
- Espionage and a treaty dividing $40 billion in oil and gas revenues
- American Ambassador thanks NSA for "deep insight into the plans and intentions" of economic negotiators.
-
Energy and Mining a focus:
- US on Brazil: NSA accused of spying on Brazilian oil company Petrobras
- Canada and US on Brazil. Brazil-Canada espionage: Which countries are we spying on? and American and Canadian Spies target Brazilian Energy and Mining Ministry
- Australia on Japan. Australian spy agency helped BHP negotiate trade deals
- Australia on East Timor Brandis orders ASIO raids related to East Timor spying case
- US on EU Obama advisor: Pipeline deals could see US spy on EU leaders
- UK on OPEC: UK spies continue “quantum insert” attack via LinkedIn, Slashdot pages
- UK on South Korea: UK targeting email of "aviation, energy, and finance sectors"
- US on Venezuela: NSA caught spying on Venezuelan oil company
- The U.S. Government's Secret Plans to Spy for American Corporations
- Why Did DOJ Indict the Chinese Military Officers?
- NSA accused of intercepting emails sent by mobile phone firm employees
- Espionnage Élysée "including the interception of all French corporate contracts and negotiations valued at more than $200 million."
- Many years. ECHELON. Search on page for "economic" and "industrial". More
- CIA Presentation On Big Data. They openly want "all human generated information."
Why doesn't GoodCrypto protect phone calls or instant messaging?
We believe it doesn't make sense to prop up a device that is a tracker and in some circumstances a bug. Obviously we are in an extreme minority on this.
What are the limitations of GoodCrypto?
Do not use GoodCrypto...
- if you don't trust your administrator. Right now anyone can spy on your mail and browsing. GoodCrypto limits that risk to the administrator you already trust.
- if you don't trust your server. A server in the cloud can be especially vulnerable.
- if you're waiting for a solution that stops every imaginable attack. There isn't one. GoodCrypto stops mass surveillance for mail and web.
- if you are a whistleblower or member of a suppressed group. GoodCrypto's metadata protection hasn't had enough field testing yet.
- if you are already encrypting mail. We don't want a monoculture.
- if you can't live without pictures, videos, etc. GoodCrypto blocks these malware vectors.
GoodCrypto keeps the content of your mail private. It is safe from prying eyes. Think of it as an envelope for your email.
GoodCrypto protects mail as it crosses the Internet. This stops mass surveillance and many targeted attacks. Your contacts can use GoodCrypto or any other OpenPGP package. Any properly configured mail server with TLS already protects between your own device and your mail server. GoodCrypto enhances your connection to add encryption, mixing, and padding between you and your contact. The result is end to end protection. Someone might possibly read your mail before it is sent, or after it arrives. But that's a lot harder.
There are tradeoffs to everything. Automatic PGP for a group requires a group key store. If your GoodCrypto server is cracked, everyone in your group is exposed. The alternative is to store private keys on relatively unprotected user machines. Public internet servers already are trusted to store private keys. Your GoodCrypto server is private, not public. It is carefully configured and protected. This is safer than users protecting themselves, which they simply don't know how to do.
Don't trust too muchPlease don't trust unencrypted communications with your life or liberty. Choose your crypto carefully. Watch for reasons to review that decision.
GoodCrypto is based on GPG and Tor. They are the safest crypto available, and are tested and trusted. But perfect crypto does not exist.
GoodCrypto has been independently audited, but needs many more independent audits. Any bug reports are very welcome.
Whatever tools you choose, any good crypto is much safer than no crypto.
How do I get my technical questions answered?
Technical FAQ, Docs, Knowledge base, Whitepaper, or just ask us.
The Technical FAQ, documentation, and the knowledge base are the most up to date documents.
There's also a whitepaper.
What should I expect after installing?
When you first install GoodCrypto, you customize it. Then you configure your existing mail server and browsers for it. Then nothing much seems to happen. GoodCrypto is almost invisible. That's what makes it so easy.
Don't expect to see anything different for local mail. That should already be protected by TLS. (If your mail server doesn't require TLS for local mail, take a few minutes now to fix that. It's important.)
As soon as someone sends their next message to anywhere, GoodCrypto generates their PGP key. You can see it on your private server's web site.
When two groups both use GoodCrypto, each person has to send one last unencrypted message to the other.
After that, the connection is encrypted. At the bottom of each message from your contact you'll see, "This message was received privately."
Here's what they didn't have to do:
- Create a key
- Publish their public key
- Find every other person's public key
- Import every other public key they need
- Encrypt and sign each outgoing message
- Decrypt and check the signature on each incoming message
GoodCrypto sends its own messages letting you know what's going on behind the scenes. At the beginning you get a message when your new key is ready. You also hear when a new public key from a contact comes in.
You can also communicate privately with anyone who uses OpenPGP. But if they aren't using GoodCrypto it's not completely automatic.
Web
Some changes when you browse are obvious at a glance. Everything looks different. The whole web appears much calmer. No pictures. No videos. No javascript. These are unfortunately all ways attackers can take over your computer without you knowing it happened. So GoodCrypto blocks them.
Some web sites are very unhappy when they can't spy on you. They complain that your browser is old or misconfigured. Ignore them.
There's also a lot you can't see. All your web traffic goes through Tor. Outgoing private information that you didn't send is stripped.
What is GoodCrypto Mail?
An email filter which encrypts and decrypts messages
GoodCrypto Mail automatically encrypts and decrypts your email when you're communicating with someone else who also uses encryption.
It takes the hassles out of key management, too, if your contacts also use GoodCrypto Mail or another application which supports automatic key exchange.
How important is email today?
182.9 Billion Emails Sent/Received Per Day Worldwide
How Much Email Do We Use Daily? 182.9 Billion Emails. Every day.
3.9 billion email accounts. 24%, or 929 million, business email accounts. Accounts are growing 6% a year.
Most email is for business. Although consumers are slowly moving to other forms of messaging, businesses use email more every year.
What problems does GoodCrypto Mail solve?
Email spying and economic espionage
Anyone can read unencrypted email
Revelations by whistleblowers like Edward Snowden have shown, that email exchanged from the privacy of our office or home, email is being scooped up by spy agencies around the world. Inside the NSA’s secret Utah data center "capable of sorting through and storing every e-mail". Wired reported that the NSA is building the country's biggest spy center and their priorities are "financial information, stock transactions, business deals".
GoodCrypto automatically encrypts and decrypts messages for everyone in your group. There's no training necessary or extra clicks. Users continue to read and write messages with their favorite mail client. GoodCrypto even manages keys automatically if the recipients also use GoodCrypto.
How does GoodCrypto Mail work?
You continue to read and write your email as usual.
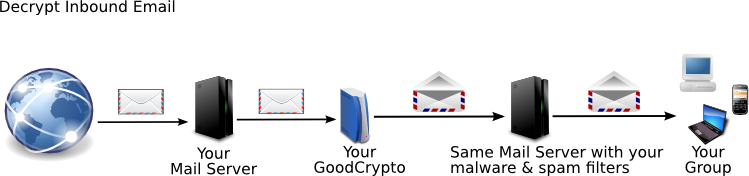
GoodCrypto Mail works between your mail server and the world, automatically making your messages private. Without GoodCrypto, anyone can read your mail. With GoodCrypto, whenever you and your contacts use GoodCrypto or other privacy software, no one can read it until it's unlocked. You don't have to do anything. You just read and write mail as usual. GoodCrypto locks and unlocks private messages for you.
Step by Step
Let's look at how mail between Ted and Alice works. Assume:
- They've never used crypto, and don't know much about it.
- They work at different companies
- Both businesses have installed GoodCrypto. GoodCrypto works with other PGP packages, too.
Ted sends a message to Alice using his favorite mail client. He doesn't do anything differently. This first message is unprotected, since Ted and Alice don't have any keys yet. The message goes to Alice immediately. Then the GoodCrypto server creates keys for Ted.
Alice responds to Ted's message. Like Ted, she sends mail exactly the way she always does. Because Ted's key isn't ready yet, this message from Alice isn't encrypted. GoodCrypto adds a note to every message telling you whether it was encrypted. Her company's GoodCrypto server creates her keys. Both Ted and Alice will receive email from the GoodCrypto server when their keys are ready.
After Ted's key is ready, when he sends Alice a message his public key will be in the header. This message is also unencrypted because Ted doesn't have Alice's key yet.
When Alice receives this message, her company's GoodCrypto server sends two notifications. One tells Alice she now has Ted's key. The other goes to the administrator to say the no-metadata key for Ted's company arrived. Both Alice and the administrator should verify these keys. Alice's GoodCrypto server also sends Ted's GoodCrypto server the no-metadata key for Alice's company.
Here's the magic. Ted and Alice didn't have to do anything. They just exchanged email as usual. No one has to remember passphrases or click extra buttons. GoodCrypto's key management creates, exchanges, and pins keys automatically. Now whenever Ted and Alice exchange a message, it's protected. Both content and metadata are encrypted, mixed, and padded. In fact, anyone in either company can send encrypted mail to anyone at the other company. The metadata protection includes its own layer of encryption. No one has to do anything.
For encryption and decryption, the GoodCrypto server never connects directly to the Internet. It only talks to your mail server. GoodCrypto benefits from any protection the mail server has.
The layers of encryption, hopefully including SMTP TLS, mean that when one layer fails you're still protected. GoodCrypto encrypts from individual to individual, then it mixes messages from one group to another, pads, and encrypts again. A well configured mail server encrypts one more time. Encryption fails over time. With layered encryption, if even one layer works, you have time to fix or replace the failed layer. If you rely on a single layer of encryption, any failure is catastrophic. A defense in depth is much safer.
Learn how GoodCrypto works if a contact does not have GoodCrypto.
Can I still exchange plain email?
Yes
Email works the way it always has, even with people who don't protect their mail.
GoodCrypto Mail adds a short note to the bottom of each insecure message you receive so you know that anyone could have read it. Learn more.
Do all my contacts have to use GoodCrypto Mail?
No
If you want your mail protected, then your contacts must use encryption software.
Does GoodCrypto Mail work with web based email?
Yes, if you control the mail server
If your company uses web based email package and manages its own mail servers, then you can use GoodCrypto Email. If you use public web based email, such as GMail or Yahoo, then you won't be able to use Mail.
Of course, if your contacts use a public web based mail, then you can still exchange email with them. It will be hard for those contacts to exchange private messages because of the hassles of most encryption solutions.
What is GoodCrypto Web?
GoodCrypto Web is a web proxy that provides tor anonimity, malware blocking, and tracker removal.
What problems does GoodCrypto Web solve?
Private and safe browsing for your organization.
Everyone in your organization browses privately through Tor. Your privacy is safe.
GoodCrypto Web also protects against malware while browsing.
Plus private information is stripped from your web requests.
How does browsing with GoodCrypto work?
Everyone continues to surf the web as usual. There's no new browser to learn.
Web access is filtered, aggregated by groups and protected by Tor after the administrator adjusts users' favorite browsers to rely on the GoodCrypto web filter.
Web requests have identifying information stripped or replaced. Incoming responses are filtered for malware vectors.
Individuals are mixed in a group. Groups are mixed by Tor. Even if someone cracks Tor, they don't know who accessed the page. They only know it was someone in a group.
And if they do identify an individual, targeted malware is blocked.