GoodCrypto Whitepaper
Overview
Solution
Threat Model
Design & Integration
Security Features
How mail works
How browsing works
Limitations
More Details
Overview
It's easy to think that when you exchange an email message or browse the web in the privacy of your office or home, no one else can see it. Prior to Edward Snowden's revelations, most of us probably thought economic espionage was just a Hollywood story line, not reality. Just a small sampling of recent news stories shows us how wrong that misconception was.
- Edward Snowden tells German TV that NSA is involved in industrial espionage. (Censored. Copies 1, 2, 3, 4)
- US and Canadian spies have targeted Brazilian companies, Petrobras and Energy and Mining Ministry.
- The Australian spy agency helped BHP negotiate trade deals.
- The Guardian reported that XKeyscore is an NSA tool that collects "nearly everything a user does on the internet".
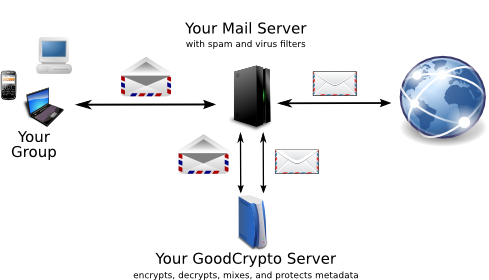
GoodCrypto stops spies from reading your email in transit and watching where you surf on the web.
Preconfigured
GoodCrypto is distributed as a preconfigured, bootable ISO. It contains all the software that you need to protect your group's mail and browsing, including full source. You simply need to integrate it with your mail server and browsers.
As years of experience with TLS, SSH, and GPG have shown, configuring crypto is hard. GoodCrypto is preconfigured to remove the hassles and improve security.
The smaller your group is, the less you can afford to install and configure your own crypto. The larger your organization is, the less you can afford users to install and configure their own crypto.
Solution: GoodCrypto Private Server
GoodCrypto is a private server that runs on your computer which protects email and browsing for a group. It automatically encrypts and decrypts email including metadata, and manages keys. Everyone in the group gets Tor anonymity plus malware blocking and tracker removal. GoodCrypto is based on the most tested and trusted crypto, GPG and Tor. Snowden relied on them, and he is alive and free. It's hard to imagine a better test.
Threat Model
GoodCrypto's threat model is global passive and active attackers.
Attackers include states, businesses, and ordinary criminals.
There is at least one global passive attacker, NSA. They strive to tap and store everything.
Counters to global passive attacks include:
- Encrypt (examples: TLS, GPG)
- Use combinatorial explosions such as mixing (examples: groups, Tor)
NSA is also the worst active attacker, although there are many. They sabotage and crack standards, products, and services. They inject packets and infect systems with malware. They embed compromised keys and bugs in hardware, at the factory and in transit.
Counters to active attacks include:
- Use tested and trusted products and services
- Avoid state sponsored standards
- Use firewalls
- Virtualize systems
Design and Integration
GoodCrypto's design is transparent protection for whole groups at a time.
Our guiding principles are:
- Protect everyone at once
No training. No clicks.
Bruce Schneier points out, "If there is anything PGP has taught us, it's that one click is one click too many." Protecting one person at a time is inefficient. You have to try to train each one to protect themselves. The success rate is not high.
Most cracked systems are user systems because ordinary people have no idea how to protect themselves online.
- Layered protection
For example, web access is filtered, aggregated by groups and protected by Tor. And, mail can be configured to use multiple encryption methods.
- Use tested and trusted components, such as GPG and Tor
We are very slow to use new protection schemes until they have been audited and their reliability proven.
- Preconfigured distribution
Just boot it. Preconfigured. Support. Security updates. Reproducible build.
- Decentralized
All your private information is on your own server. Automatic key management with no central servers. P2P public key distribution. Key pinning.
- Integrate with existing mail and browsers
Uses the same SMTP, IMAP, and POP servers you use now. Same mail clients and browsers. Same antispam and antivirus. Integrates at the MTA level.
- Don't use known compromised encryption
This may seem obvious, but some compromised crypto is standard. State sponsored standards are generally crippled so the state can crack them, which of course means others can crack them.
- Don't trust too much
That includes us. Encourage people to audit GoodCrypto. The goal is to be tested and trusted, not blindly trusted.
- Virtualization to protect against embedded malware
Ed Snowden says that VMs are "a big step up" against persistent threats. That matches our experience.
Special Security Features
![]() Encrypts content and metadata
It's easy to understand how someone who can read your mail gains
a lot of valuable information about your business deals,
financial data and more. As articles in
The Guardian
and
Wired
showed, metadata (i.e., sender and recipient addresses, subjects, etc.) reveals much more
private information about you than you might realize. The ex-NSA chief admitted that
"We kill people based on metadata."
GoodCrypto lets you protect both metadata and content.
Encrypts content and metadata
It's easy to understand how someone who can read your mail gains
a lot of valuable information about your business deals,
financial data and more. As articles in
The Guardian
and
Wired
showed, metadata (i.e., sender and recipient addresses, subjects, etc.) reveals much more
private information about you than you might realize. The ex-NSA chief admitted that
"We kill people based on metadata."
GoodCrypto lets you protect both metadata and content.
![]() Mixes and packetizes messages to resist both network and traffic analysis
You can protect your connections with others even more by using GoodCrypto's
bundling and packetization. Messages between two domains are sent in padded and encrypted bundles on a regular
schedule. So no one knows which individuals in the companies are communicating,
how often, or even whether messages are long or short. GoodCrypto encrypts each individual message,
then periodically bundles all messages that are going to the other domain, pads the new combined
message, and finally encrypts the entire bundle. If no one has a message for the
other domain, GoodCrypto still sends a padded encrypted message. Snoops don't know if anyone is actually talking.
Mixes and packetizes messages to resist both network and traffic analysis
You can protect your connections with others even more by using GoodCrypto's
bundling and packetization. Messages between two domains are sent in padded and encrypted bundles on a regular
schedule. So no one knows which individuals in the companies are communicating,
how often, or even whether messages are long or short. GoodCrypto encrypts each individual message,
then periodically bundles all messages that are going to the other domain, pads the new combined
message, and finally encrypts the entire bundle. If no one has a message for the
other domain, GoodCrypto still sends a padded encrypted message. Snoops don't know if anyone is actually talking.
![]() Pins keys
GoodCrypto includes the sender's key in the header
of every message. Whenever a message arrives from
someone else using GoodCrypto, the key is verified
that it matches the key in your local database. That
way someone can't fake sending an encrypted message from someone else.
Pins keys
GoodCrypto includes the sender's key in the header
of every message. Whenever a message arrives from
someone else using GoodCrypto, the key is verified
that it matches the key in your local database. That
way someone can't fake sending an encrypted message from someone else.
![]() Blocks web malware
GoodCrypto's web proxy strips images and other malware vectors so your users'
computers aren't infected.
Blocks web malware
GoodCrypto's web proxy strips images and other malware vectors so your users'
computers aren't infected.
![]() Resists user tracking
Everyone's web requests can automatically be routed through Tor so it's
difficult to track what sites users visit. By sharing the same Tor connection,
everyone in your company's web activity is aggregated which amplifies the
protection against tracking of online activity.
Resists user tracking
Everyone's web requests can automatically be routed through Tor so it's
difficult to track what sites users visit. By sharing the same Tor connection,
everyone in your company's web activity is aggregated which amplifies the
protection against tracking of online activity.
![]() Your administrator runs our software on your server
We strongly recommend that you install your GoodCrypto private
server on a headless machine. It is fully self-contained with no
SSH access. Your administrator manages your GoodCrypto private server
via the web with no interface to keys, passphrases, or messages.
Your administrator runs our software on your server
We strongly recommend that you install your GoodCrypto private
server on a headless machine. It is fully self-contained with no
SSH access. Your administrator manages your GoodCrypto private server
via the web with no interface to keys, passphrases, or messages.
All encryption and decryption happens on your servers. Your administrator manages your mail just like always.
![]() All private keys and passphrases stay on your server
You don't need to trust any thirdparty. You
can secure your GoodCrypto private server to meet your standards --
not rely on others.
All private keys and passphrases stay on your server
You don't need to trust any thirdparty. You
can secure your GoodCrypto private server to meet your standards --
not rely on others.
Any government requests for encryption keys comes to your company so you'll know if the keys are no longer secure.
![]() Easy verification that email was decrypted by your GoodCrypto private server
You can click on a tag added to each decrypted message to verify the message
was decrypted by your GoodCrypto private server. This ensures that someone doesn't
simply add a tag to a regular message to mislead you into thinking it arrived privately.
Easy verification that email was decrypted by your GoodCrypto private server
You can click on a tag added to each decrypted message to verify the message
was decrypted by your GoodCrypto private server. This ensures that someone doesn't
simply add a tag to a regular message to mislead you into thinking it arrived privately.
![]() Open source so anyone can audit code
All of the source code we've written for this project is open source and included
with every distribution. Plus we rely on other open source projects for the
crypto (GPG and Tor) and the OS itself (Linux). We encourage anyone with the skill
to audit our software and publish the results.
Open source so anyone can audit code
All of the source code we've written for this project is open source and included
with every distribution. Plus we rely on other open source projects for the
crypto (GPG and Tor) and the OS itself (Linux). We encourage anyone with the skill
to audit our software and publish the results.
![]() Warning if message signed by user other than SMTP sender
GoodCrypto verifies that a signed message was signed by the SMTP sender and reports
if it's not. The SMTP sender is not always the same user as the one that appears in
the header of a message so if someone is trying to trick you into believing a message
was signed by someone it wasn't, GoodCrypto will help you spot the attempted deception.
Warning if message signed by user other than SMTP sender
GoodCrypto verifies that a signed message was signed by the SMTP sender and reports
if it's not. The SMTP sender is not always the same user as the one that appears in
the header of a message so if someone is trying to trick you into believing a message
was signed by someone it wasn't, GoodCrypto will help you spot the attempted deception.
![]() Sender notification when new key received or created
GoodCrypto sends an email message whenever a new key from a sender is received.
It also reminds you to verify the key id with the sender so you can be confident
you're communicating privately with the person you think you are instead of a
man-in-the-middle.
Sender notification when new key received or created
GoodCrypto sends an email message whenever a new key from a sender is received.
It also reminds you to verify the key id with the sender so you can be confident
you're communicating privately with the person you think you are instead of a
man-in-the-middle.
How GoodCrypto mail works
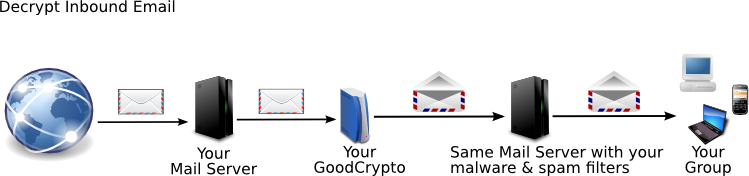
GoodCrypto Mail works between your mail server and the world, automatically making your messages private. Without GoodCrypto, anyone can read your mail. With GoodCrypto, whenever you and your contacts use GoodCrypto or other privacy software, no one can read it until it's unlocked. You don't have to do anything. You just read and write mail as usual. GoodCrypto locks and unlocks private messages for you.
Step by Step
Let's look at how mail between Ted and Alice works. Assume:
- They've never used crypto, and don't know much about it.
- They work at different companies
- Both businesses have installed GoodCrypto. GoodCrypto works with other PGP packages, too.
Ted sends a message to Alice using his favorite mail client. He doesn't do anything differently. This first message is unprotected, since Ted and Alice don't have any keys yet. The message goes to Alice immediately. Then the GoodCrypto server creates keys for Ted.
Alice responds to Ted's message. Like Ted, she sends mail exactly the way she always does. Because Ted's key isn't ready yet, this message from Alice isn't encrypted. GoodCrypto adds a note to every message telling you whether it was encrypted. Her company's GoodCrypto server creates her keys. Both Ted and Alice will receive email from the GoodCrypto server when their keys are ready.
After Ted's key is ready, when he sends Alice a message his public key will be in the header. This message is also unencrypted because Ted doesn't have Alice's key yet.
When Alice receives this message, her company's GoodCrypto server sends two notifications. One tells Alice she now has Ted's key. The other goes to the administrator to say the no-metadata key for Ted's company arrived. Both Alice and the administrator should verify these keys. Alice's GoodCrypto server also sends Ted's GoodCrypto server the no-metadata key for Alice's company.
Here's the magic. Ted and Alice didn't have to do anything. They just exchanged email as usual. No one has to remember passphrases or click extra buttons. GoodCrypto's key management creates, exchanges, and pins keys automatically. Now whenever Ted and Alice exchange a message, it's protected. Both content and metadata are encrypted, mixed, and padded. In fact, anyone in either company can send encrypted mail to anyone at the other company. The metadata protection includes its own layer of encryption. No one has to do anything.
For encryption and decryption, the GoodCrypto server never connects directly to the Internet. It only talks to your mail server. GoodCrypto benefits from any protection the mail server has.
The layers of encryption, hopefully including SMTP TLS, mean that when one layer fails you're still protected. GoodCrypto encrypts from individual to individual, then it mixes messages from one group to another, pads, and encrypts again. A well configured mail server encrypts one more time. Encryption fails over time. With layered encryption, if even one layer works, you have time to fix or replace the failed layer. If you rely on a single layer of encryption, any failure is catastrophic. A defense in depth is much safer.
Learn how GoodCrypto works if a contact does not have GoodCrypto.
Learn how GoodCrypto protects metadata.
How GoodCrypto browsing works
Everyone continues to surf the web as usual. There's no new browser to learn.
Web access is filtered, aggregated by groups and protected by Tor after the administrator adjusts users' favorite browsers to rely on the GoodCrypto web filter.
Web requests have identifying information stripped or replaced. Incoming responses are filtered for malware vectors.
Individuals are mixed in a group. Groups are mixed by Tor. Even if someone cracks Tor, they don't know who accessed the page. They only know it was someone in a group.
And if they do identify an individual, targeted malware is blocked.
Limitations
Do not use GoodCrypto...
- if you don't trust your administrator. Right now anyone can spy on your mail and browsing. GoodCrypto limits that risk to the administrator you already trust.
- if you don't trust your server. A server in the cloud can be especially vulnerable.
- if you're waiting for a solution that stops every imaginable attack. There isn't one. GoodCrypto stops mass surveillance for mail and web.
- if you are a whistleblower or member of a suppressed group. GoodCrypto's metadata protection hasn't had enough field testing yet.
- if you are already encrypting mail. We don't want a monoculture.
- if you can't live without pictures, videos, etc. GoodCrypto blocks these malware vectors.
GoodCrypto keeps the content of your mail private. It is safe from prying eyes. Think of it as an envelope for your email.
GoodCrypto protects mail as it crosses the Internet. This stops mass surveillance and many targeted attacks. Your contacts can use GoodCrypto or any other OpenPGP package. Any properly configured mail server with TLS already protects between your own device and your mail server. GoodCrypto enhances your connection to add encryption, mixing, and padding between you and your contact. The result is end to end protection. Someone might possibly read your mail before it is sent, or after it arrives. But that's a lot harder.
There are tradeoffs to everything. Automatic PGP for a group requires a group key store. If your GoodCrypto server is cracked, everyone in your group is exposed. The alternative is to store private keys on relatively unprotected user machines. Public internet servers already are trusted to store private keys. Your GoodCrypto server is private, not public. It is carefully configured and protected. This is safer than users protecting themselves, which they simply don't know how to do.
Don't trust too muchPlease don't trust unencrypted communications with your life or liberty. Choose your crypto carefully. Watch for reasons to review that decision.
GoodCrypto is based on GPG and Tor. They are the safest crypto available, and are tested and trusted. But perfect crypto does not exist.
GoodCrypto has been independently audited, but needs many more independent audits. Any bug reports are very welcome.
Whatever tools you choose, any good crypto is much safer than no crypto.