FAQ: General Questions & Answers
How does GoodCrypto Mail work?
You continue to read and write your email as usual.
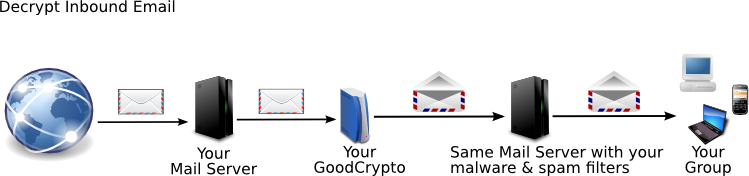
GoodCrypto Mail works between your mail server and the world, automatically making your messages private. Without GoodCrypto, anyone can read your mail. With GoodCrypto, whenever you and your contacts use GoodCrypto or other privacy software, no one can read it until it's unlocked. You don't have to do anything. You just read and write mail as usual. GoodCrypto locks and unlocks private messages for you.
Step by Step
Let's look at how mail between Ted and Alice works. Assume:
- They've never used crypto, and don't know much about it.
- They work at different companies
- Both businesses have installed GoodCrypto. GoodCrypto works with other PGP packages, too.
Ted sends a message to Alice using his favorite mail client. He doesn't do anything differently. This first message is unprotected, since Ted and Alice don't have any keys yet. The message goes to Alice immediately. Then the GoodCrypto server creates keys for Ted.
Alice responds to Ted's message. Like Ted, she sends mail exactly the way she always does. Because Ted's key isn't ready yet, this message from Alice isn't encrypted. GoodCrypto adds a note to every message telling you whether it was encrypted. Her company's GoodCrypto server creates her keys. Both Ted and Alice will receive email from the GoodCrypto server when their keys are ready.
After Ted's key is ready, when he sends Alice a message his public key will be in the header. This message is also unencrypted because Ted doesn't have Alice's key yet.
When Alice receives this message, her company's GoodCrypto server sends two notifications. One tells Alice she now has Ted's key. The other goes to the administrator to say the no-metadata key for Ted's company arrived. Both Alice and the administrator should verify these keys. Alice's GoodCrypto server also sends Ted's GoodCrypto server the no-metadata key for Alice's company.
Here's the magic. Ted and Alice didn't have to do anything. They just exchanged email as usual. No one has to remember passphrases or click extra buttons. GoodCrypto's key management creates, exchanges, and pins keys automatically. Now whenever Ted and Alice exchange a message, it's protected. Both content and metadata are encrypted, mixed, and padded. In fact, anyone in either company can send encrypted mail to anyone at the other company. The metadata protection includes its own layer of encryption. No one has to do anything.
For encryption and decryption, the GoodCrypto server never connects directly to the Internet. It only talks to your mail server. GoodCrypto benefits from any protection the mail server has.
The layers of encryption, hopefully including SMTP TLS, mean that when one layer fails you're still protected. GoodCrypto encrypts from individual to individual, then it mixes messages from one group to another, pads, and encrypts again. A well configured mail server encrypts one more time. Encryption fails over time. With layered encryption, if even one layer works, you have time to fix or replace the failed layer. If you rely on a single layer of encryption, any failure is catastrophic. A defense in depth is much safer.
Learn how GoodCrypto works if a contact does not have GoodCrypto.